Azure Advisor And Fixing Errors
Azure can be configured to send you advisor reports detailing things that are not quite right in your environment. The advisor is not necessarily always right but it’s sensible to review the outputs periodically, even if they relate to non production environments.
A few issues popped up on an advisor report on my recent travels and although you can just use the entries on the report on the portal to target the offending resources, I thought it might be helpful to write some Powershell to identify the offending resources as an alternative.
Secure transfer to storage accounts should be enabled
This error shows up similar to this on the report:

Fairly obvious what this means really – the storage account has a setting which is currently set to allow insecure transfers (via http rather than https) – an example looks like this under the Configuration blade of the Storage Account:
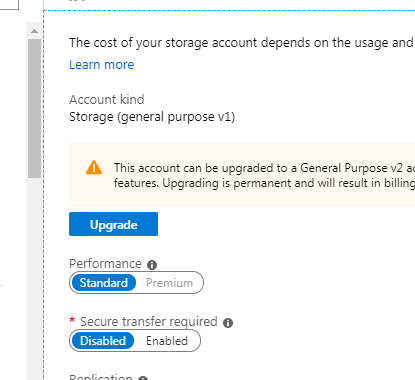
The advisor highlights this and the solution is to just set the toggle to Enabled for “Secure transfer required” and press save.
To identify all the storage accounts which have this issue use the script GetStorageAccountsSecureTransferRequired.ps1
This gives output similar to the following (redacted):
StorageAccountName ResourceGroupName Location SkuName Kind AccessTier CreationTime ProvisioningState EnableHttps TrafficOnly
—————— —————– ——– ——- —- ———- ———— —————– ———–
XXXXXXXXXXXXXXXXXX AAAAAAAAAAAAAAA northeurope Standard_LRS Storage 9/6/19 9:51:53 PM Succeeded False
YYYYYYYYYYYYYYYYYY AAAAAAAAAAAAAAA northeurope Standard_LRS Storage 6/26/19 3:29:38 PM Succeeded False
An Azure Active Directory
administrator should be
provisioned for SQL servers
This one appears like the following in the advisor output:

As a long term Oracle guy I’m no SQL Server expert so I can’t quite see why this is an issue if you have a SQL Server authenticated administrative user active – no doubt a friendly SQL DBA will chime in and explain.
To fix this navigate to the SQL Server in question and the Active Directory admin blade and select “Set admin”, choose a user from the Active Directory and press Save.
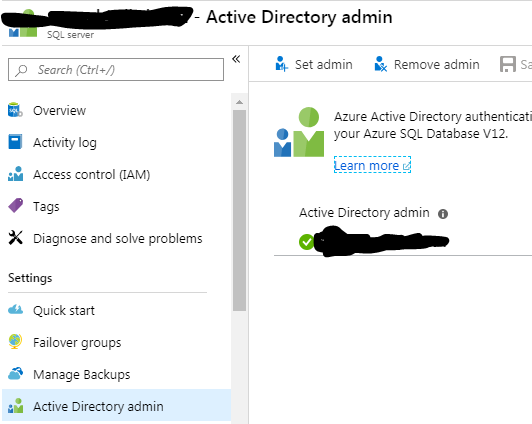
To find all SQL Servers affected by this use the script GetSQLServerWithoutAADAdministrator.ps1
This returns output similar to the following (redacted):
mysqlserver1 mysqlserver2 mysqlserver3 mysqlserver4
Enable virtual machine backup to
protect your data from corruption
and accidental deletion
This one appears like the following in the advisor output:

To fix this, navigate to the Backup blade on the VM Resource in question and set the appropriate settings to enable the backup.
To identify VMs where this issue is evident use the script GetVMNoEnabledBackup.ps1
This gives results similar to the following, allowing you to see VMs where no backup is enabled:
myvm2 myvm3